Consulting
Advanced consulting services for individuals, companies, and public administrations
The Let's Guard It! consulting services focus on cybersecurity risk analysis and treatment: a fundamental tool for any organization to adopt a strategy that implements the best protection measures for their business. Cyber attacks and incidents can occur in countless ways and have devastating effects on organizations without a comprehensive prevention, protection, and mitigation strategy.
The context
According to the most recent analysis by the International Monetary Fund, the number of cyber incidents/attacks and the risk of the related economic losses has increased exponentially over the last 20 years.
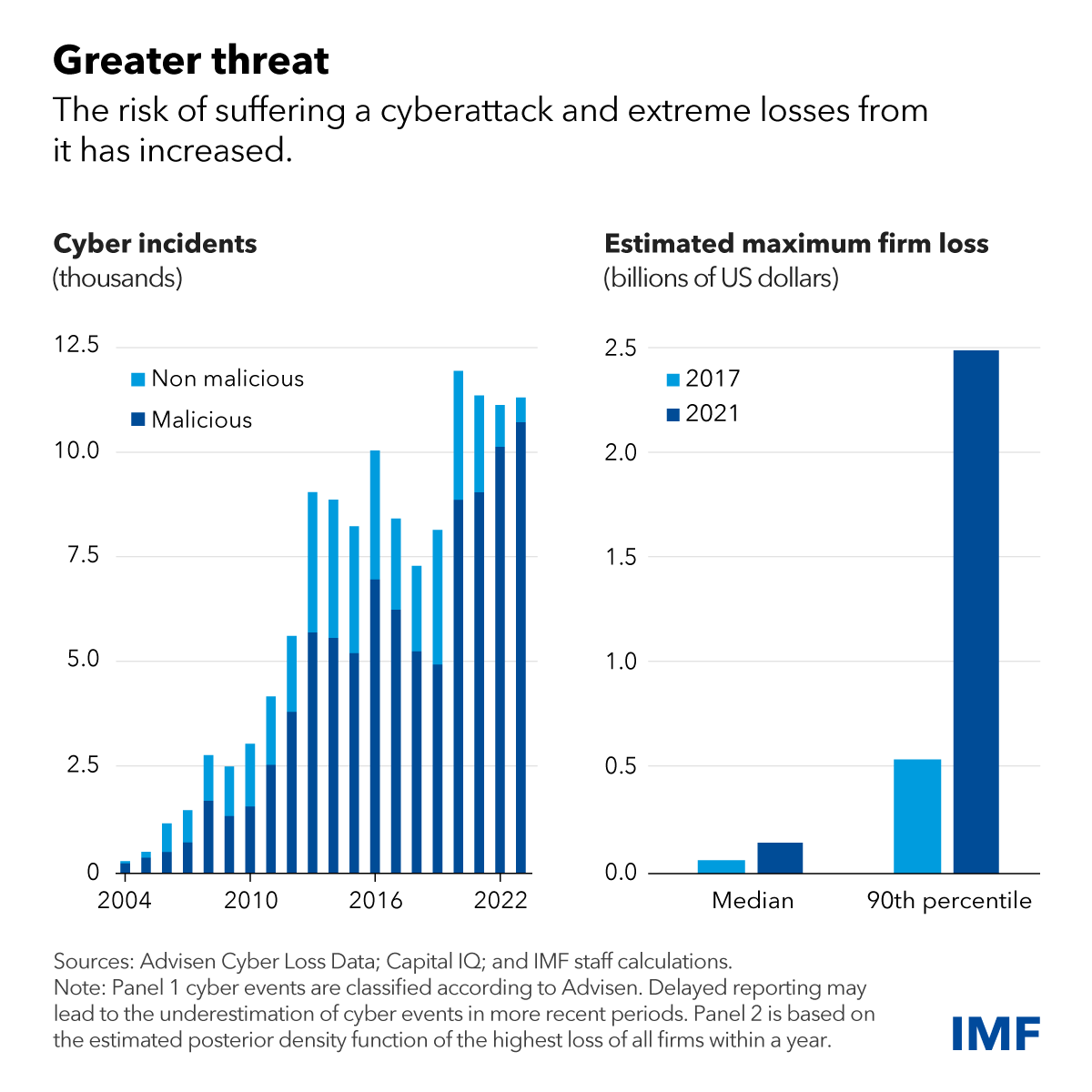
It is difficult to make precise estimates, but the cost of a cyber breach can range from several thousand to several million US dollars/euros, depending on a lot of parameters.
IBM's 2025 Cost of a Data Breach Report highlights that the average cost of a single data breach for companies is approximately $4.4 million, which can rise to $9 million USD for those subject to more stringent constraints (such as those operating in the healthcare sector). These costs can be categorized as:
- direct, for incident response, recovery of system functionality, payment of any ransoms (e.g. in the case of ransomware), audit activities and system updates;
- indirect, due to loss of revenue (e.g. in the event of a service failure), damage to reputation, legal actions and sanctions due to violations of regulations, increased insurance costs, costs due to business interruption in related areas.
The solution
To manage this issue, it is essential to have a risk mitigation strategy tailored to your organization. Risk analysis and management is also at the core of major international standards, such as ISO 27001, payment standards like PCI-DSS, as well as regulations applicable to critical service providers like NIS2.
As part of the service, we will assist you in drafting or revising the plan for:
- vulnerability detection, which defines procedures, tools and mechanisms for identifying and reporting security vulnerabilities;
- vulnerability management, which defines procedures for vulnerability management, metrics and target values for monitoring the process;
- incident response, which identifies actors, tools and procedures for the correct management of IT incidents.
Where applicable, our Service may also provide advice on the analysis and treatment of risks associated with the use or implementation of AI-based tools.